"Mobile attacks and vulnerabilities are increasing in terms of both number and pragmatism."
This statement made by the Gartner within the “Predicts 2017: Endpoint and mobile security” report is the foundation of the Mobile Threat Defense and the Mobile Application Security Testing Gartner’s 2017 market guides.If the needs behind Mobile Application Security and Endpoint Security underlie distinct use cases, both are about revealing, qualifying and preventing from mobile security flaws and ultimately trigger the same technology principles.
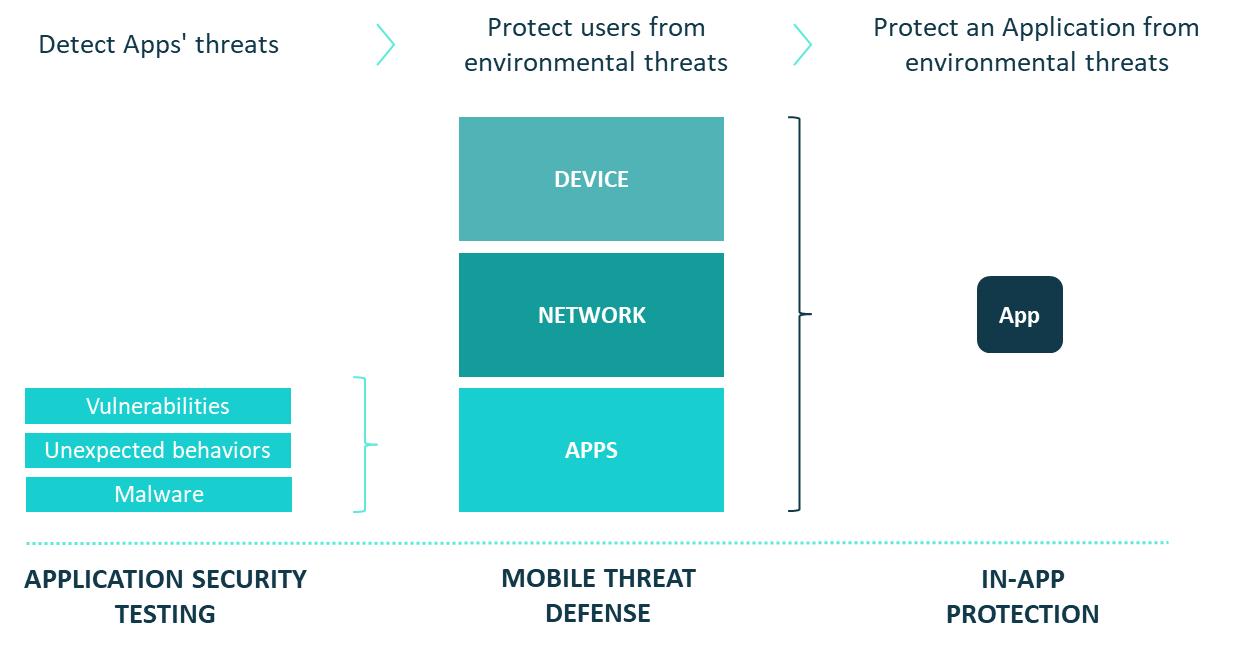
MOBILE APPLICATION SECURITY TESTING (MAST): REVEAL APPS’ NATURE
We outlined in this Application Security Guide two categories of threats to be managed from an Application perspective: Inside threats and environmental threats.
Inside threats represents the first category to be handled using an Application Security Testing tool. Such solution aims to identify vulnerabilities or unexpected behaviors that have been embedded into an Application and to provide guidance on mitigation actions.
In this article, Mobile Application Security Testing, A must do, we presented the whys and the wherefores that should be covered by the Application security testing tools in order to face adequate requirements.
From a business perspective, Mobile Application Security Testing usually answers one of the needs below:
- Validating Applications to be published on private stores: Some companies opted for a closed mobile environment, where users cannot access to public stores and rely on a private store to download selected Applications. In this configuration, the MAST tool will help companies to verify the compliancy of an Application against their own security policy and approve it with a top-down approach.
- Check Application Security as part of the DevOps process: When developing Applications whether for corporate or business needs, companies require to validate the security levels of their Applications. Security expectations driven by internal requirements and regulations combined with short go-to-market lead times prompt companies to rely on automated tools to be integrated as part of their validation process.
From a technical stand point, Mobile Application Security Testing involves an advanced expertise on Applications analysis in order to properly dissect behaviors and highlight vulnerabilities. The accuracy of the technology is key to deliver an appropriate service where there is no room for false positive.
MOBILE THREAT DEFENSE (MTD): WARD-OFF ENVIRONMENTAL THREATS
Mobile endpoint security is about detecting and managing mobile threats from the device.
Those threats are usually classified into 3 structuring families:
- Leaky and Malicious Applications (malwares, data leakage or corruption, …)
- OS Manipulations (OS vulnerability exploit, priviledge escalation hiding, …)
- Network Exploits (rogue connections, Man-In-The-Middle, …)
Mobile Threat Defense solutions deal with the business need to protect corporate users. From Enterprise Mobile Management platform update, to on-device agent, they offer different options and security levels to secure corporate users in alignment with the company policy.
The detection of leaky and malicious Applications directly involves the same expertise and capabilities as for Mobile Application Security Testing. Therefore, Mobile Threat Defense consists in adding network and device threat management bricks to the mobile security wall.
IN-APP PROTECTION: THE BRIDGE BETWEEN MAST AND MTD
Mobile Application Security Testing cleans Applications from inside threats whereas Mobile Threat Defense protects users from environmental threats.
The last use case which is not addressed is about protecting an App from the on-device environmental threats. Actually, an App running onto unmanaged devices remains vulnerable to its environment (malwares, network exploits,…) and sensitive data could be retrieved.
The In-App protection covers this ultimate requirement and provides, via an SDK to be embedded within the App, an on-device protection allowing the App to adjust its behaviors and the service level offered to the user according to real time threats.
The In-App Protection covers the exact same threat perimeter as Mobile Threat Defense, with the only difference being that protective actions are directly managed from the protected app.
Discover Pradeo's solutions:


.png)



