Updated on June 7th: Following the announcement of these discoveries, the "Peel Smart Remote" mobile application was removed from Google Play.
The Peel Smart Remote app is a widely used Google Play application (100M+ installs) that has often made the news because of its highly intrusive behaviors, such as full screen overlays and untimely advertising, causing poor user experience.
Last week, the Pradeo Security engine alerted its users about severe security issues discovered in the app’s 10.7.3.3 version. It has been found that the application collects and leaks users’ pictures to a server that does not belong to the app publisher. Last Friday, the application was updated on the Google Play store (now version 10.7.4.2), the leaky behavior has been removed from the code but yet no communication was made by the company on this matter. Because applications’ update is not automatic on all Android devices, millions of users running the former version of the app are still currently exposed.
Pictures leaked to an externally owned server
The Peel Smart Remote 10.7.3.3 version is programmed to send pictures contained in devices’ external storage to a server that does not belong to Peel Technologies. To prevent pictures from being breached, the Pradeo Lab advises anyone who uses this application to update it to its latest available version.
Data collection
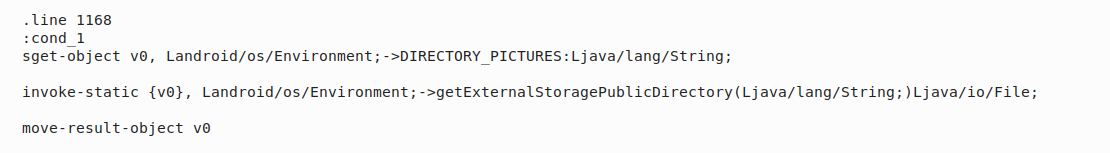
Data sending
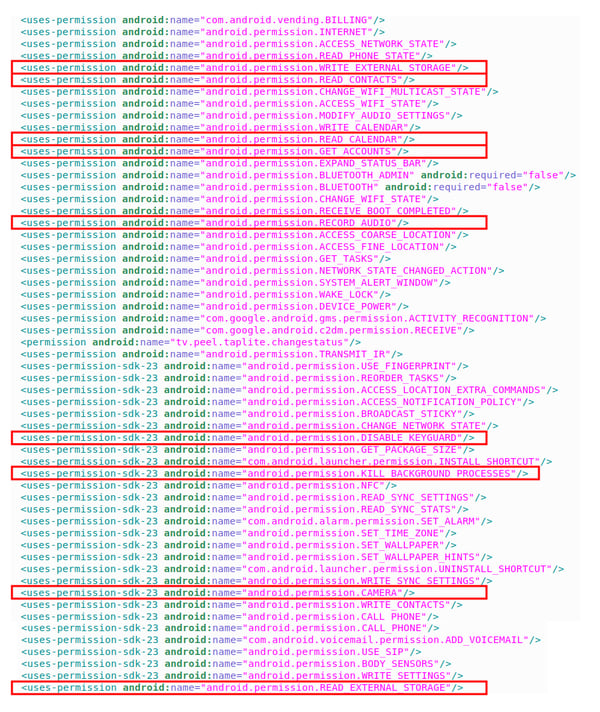
A massive list of permission requests
To access users’ pictures, the Peel Smart Remote application uses the following permissions:
Android.permission.WRITE_EXTERNAL_STORAGE
Android.permission.READ_EXTERNAL_STORAGE
According to the official Android app developers’ documentation, “External storage is the best place for files that don't require access restrictions and for files that you want to share with other apps or allow the user to access with a computer”. By writing anything on external storage, the Peel Smart Remote app highly exposes its users’ data. By reading it, it accesses users’ pictures, video, audio and any other files stored on it.
Besides, it’s interesting to note that the application asks for critical permissions providing access to the camera, the contact list, the calendar and even allowing to record the audio. Although, these permissions don’t seem to be required for the use of the remote.
Android.permission.CAMERA
Android.permission.READ_CONTACTS
Android.permission.READ_CALENDAR
Android.permission.RECORD_AUDIO
Peel Smart Remote permission requests
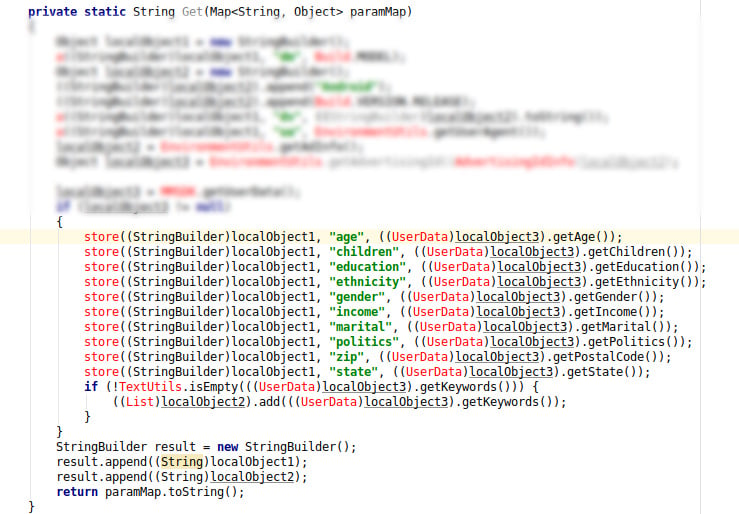
Other sensitive information sent over the network
To finish, it appears in the report provided by the Pradeo Security engine that the application collects personal information such as users’ age, ethnicity, income, political orientations, etc., and sends them over the network.
Data collection
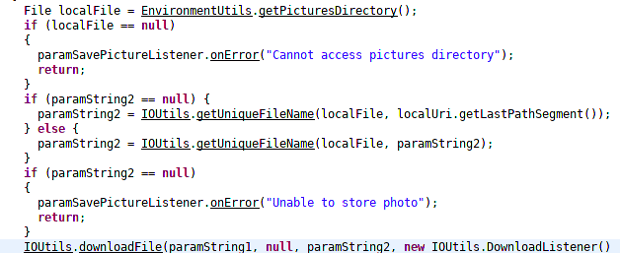
Data sending
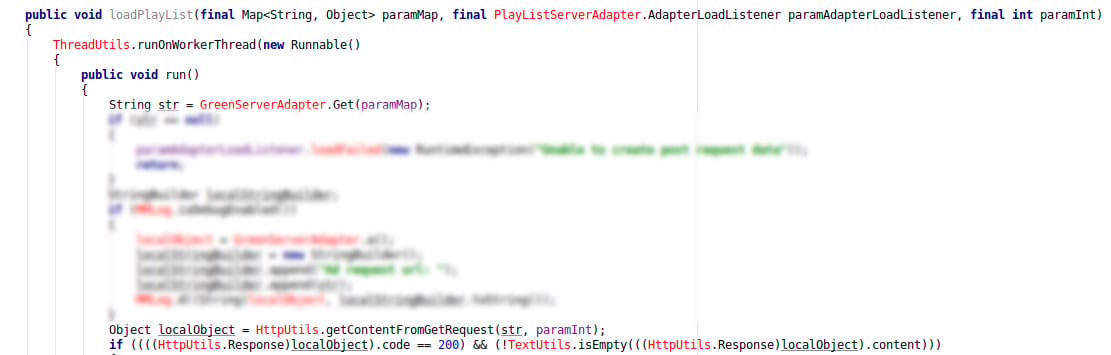
The original code of the Peel Smart Remote is obfuscated by a tool (Proguard) that changes the functions’ name by letters, making them harder to understand at a human scale. In the 2 last screenshots, we replaced the obfuscated names by words describing the functions, to ease the understanding.
Application ID
Package name: tv.peel.smartremote
Version: 10.7.3.3
Installs: 100M+
Developer: Peel Technologies

.png)


