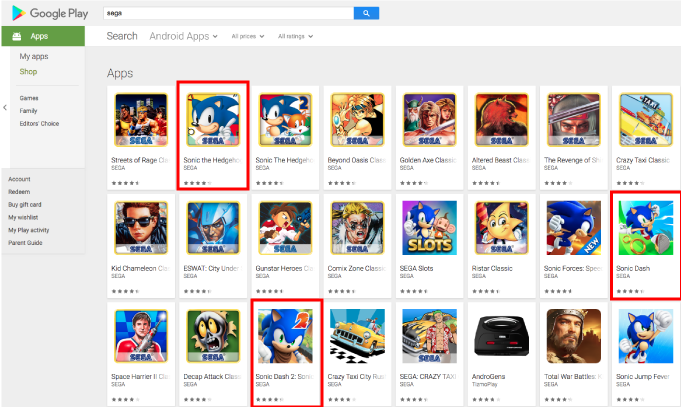
Pradeo’s Lab discovered that some game applications in the Google Play published by SEGA, the famous video games developer and publisher, access and leak users’ geolocation and device data. Hundreds of millions of users are concerned by these data privacy violations.
The affected android apps are the following ones:
- Sonic Dash - 100 to 500 millions downloads
- Sonic the Hedgehog™ Classic - 10 to 50 millions downloads
- Sonic Dash 2: Sonic Boom - 10 to 50 millions downloads
By analyzing the aforementioned apps, we identified these common facts:
- The 3 Apps geolocate users and relay their position
- The 3 Apps leak device data
- Data are sent to an average of 11 distant servers including 3 uncertified ones
- The 3 Apps feature an average of 15 OWASP vulnerabilities
Data privacy violations
Lately, the Pradeo Lab noticed an increase in the amount of official apps fooling their users into giving them access to data they don’t actually need. In most of the cases, when installing an app from Google Play, users accept permissions without giving a second thought. As a result, publishers collect private information about their clients, such as geolocation, device data, users data (gallery, contact lists, browser history, SMS…), etc.
In this case, the 3 SEGA apps collect and leak geolocation and device data to several distant servers, including suspicious ones.
Data sent to uncertified servers
Among the distant servers reached by the affected SEGA apps when sending data, we can see that most have a tracking and marketing purpose. However, what caught Pradeo’s researchers attention is the fact that these apps are sending information to 3 uncertified servers which represent a potential threat.
Several critical OWASP vulnerabilities
Among the vulnerabilities detected in the analyzed SEGA apps, we identified two critical ones that make them highly vulnerable to Man-In-The-Middle attacks (X.509TrustManager and PotentiallyByPassSslConnection). The other OWASP vulnerabilities detected can result in denial of service, sensitive data leakage and clearly show encryption weaknesses.
Apps ID:
Sonic Dash - Package: com.sega.sonicdash - SHA1 : d7fc33843fab48666bafb85392e2d1cd4f116e6b
Sonic the Hedgehog™ Classic - Package: com.sega.sonic1px - SHA1 : 0b1b33cdbc71ff07e6a76a9b425e534a64a005c9
Sonic Dash 2: Sonic Boom - Package: com.sega.sonicboomandroid - SHA1 : a54fadc572e9ef12d07dd61230d41fcbe3f24e17
Leaked data:
- Geolocation
- Mobile network information: Service provider name, network type (3G, 4G, UMTS…)
- Device information: Manufacturer, commercial name -e.g.:Nexus 4), Battery level, Maximum level of battery, Operating System version number
OWASP vulnerabilities detected:
| BROADCAST-ACTIVITY | The vulnerability gives permission to other applications to bypass some security access, to give direct access to potentially sensitive data. |
|
BROADCAST-SERVICE |
The vulnerability gives permission to other applications the power to start or bind the application's service. Using the flaw can lead to sensitive information leakage towards malicious apps or result in denial of service. |
|
BROADCST-RECEIVER |
The vulnerability gives permission to other applications to send malicious intent to the application. Acting on receipt of intent without validating the caller's identity may lead to sensitive data being revealed or to denial of service. |
|
URLCANONICALISATION |
Makes easier for another application to access your application data (file). Depending on the implementation of Content Provider, use of the method can lead to a directory traversal vulnerability. |
| LOG |
Applications should make sure that they do not send sensitive information to log output. |
|
IMPLICIT-INTENT |
A malicious activity or service can intercept an implicit intent and be started instead of the intended activity or service. This could result in the interception of data or in a denial of service. |
|
X.509TRUSTMANAGER |
Unsafe implementation of the interface X509TrustManager. Specifically, the implementation ignores all SSL certificate validation errors when establishing an HTTPS connection to a remote host, thereby making your app vulnerable to man-in-the-middle attacks. An attacker could read transmitted data (such as login credentials) and even change the data transmitted on the HTTPS connection. |
|
POTENTIALLY_BYPASS SSL_CONNECTION |
The implementation bypasses all SSL certificate validation errors when establishing an HTTPS connection to a remote host, thereby making your app vulnerable to man-in-the-middle attacks. An attacker could read transmitted data (such as login credentials) and even change the data transmitted on the HTTPS connection |
|
D_ROOTCHECK |
This App may have root detection capabilities. |
| D_WEBVIEWDEBUG |
Remote WebView debugging is enabled. |
| D_SQLITE |
App uses SQLite Database and execute raw SQL query. Untrusted user input in raw SQL queries can cause SQL Injection. Also sensitive information should be encrypted and written to the database. |
| D_EXTSTORAGE |
App can read/write to External Storage. Any App can read data written to External Storage. |
| D_TMPFILE |
App creates temp file. Sensitive information should never be written into a temp file. |
| D_JSENABLED |
Insecure WebView Implementation. Execution of user controlled code in WebView is a critical Security Hole. |
| SQLC_PASSWORD |
This App uses SQL Cipher. But the secret may be hardcoded. |
| D_CON_WORLD_READABLE |
The file is World Readable. Any App can read from the file. |
| WORLD-READABLE |
It should not be possible for other apps to be able to access this data, or for the data to be accessible to other programs or people, if the data owner does not intend that. |
| ECB |
The App uses ECB mode in Cryptographic encryption algorithm. ECB mode is known to be weak as it results in the same ciphertext for identical blocks of plaintext. |


.png)


