Do you usually install your airline mobile app when traveling? You may think twice before using it for your next vacation.
Our latest study based on the security testing of global top 50 airline mobile applications shed the light on some alarming data privacy concerns. The audit was performed this week by Pradeo Security, an engine designed to reveal mobile apps’ behaviors (data processing) and vulnerabilities. Among the 50 mobile applications tested, had been included the most used ones globally, mainly from North America, Western Europe and Eastern Asia.
Personal and financial data sent over the network through non-certified connections
To provide users with the best services, airlines enable their applications with functionalities to scan passports and credit cards, check-in, make mobile payments, consult boarding passes, etc. This study shows that at least 49% of airline applications manipulate users’ location information, gallery, and contact list. Then, a third of them send the personal data in question over the network. Besides, what’s even more surprising is that most of the time, the transmission is performed through non-certified connections, thus highly facilitating data theft. The study reports that airline applications use an average of 14 unsecure connections to servers.
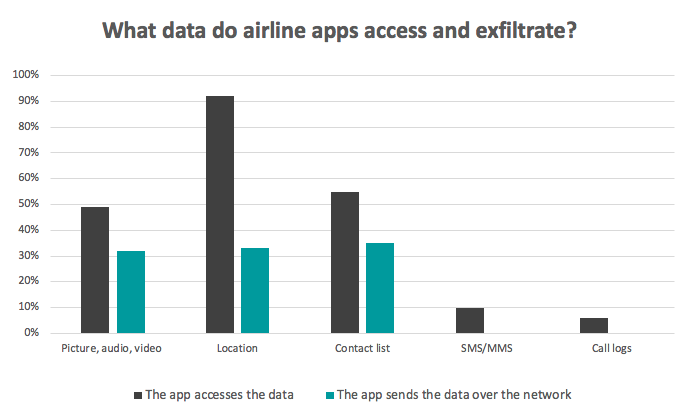
Code vulnerabilities weakening the apps resistance to common attacks
Short go-to-market processes often lead to code negligence regarding security. In the audited sample, we found an average of 21 vulnerabilities per application, a very high number when put in conjunction with the sensitivity of the information manipulated (passport, credit card…). The 10 code vulnerabilities most detected among the sample are known for greatly exposing applications to denial of service, data leakage and man-in-the-middle attacks.
Top 10 vulnerabilities (detailed below):
- Broadcast activity 98%
- DSQLite 94%
- Broadcast receiver 92%
- SQLC_password 90%
- Implicit intent 88%
- Broadcast service 86%
- d_JSenabled 78%
- d_external storage 66%
- d_webviewdebug 47%
- HandleSslError 16%
BROADCAST-ACTIVITY
The vulnerability gives permission to other applications to bypass some security access, to give direct access to potentially sensitive data.
D_SQLITE
App uses SQLite Database and execute raw SQL query. Untrusted user input in raw SQL queries can cause SQL Injection. Also sensitive information should be encrypted and written to the database.
BROADCAST-RECEIVER
The vulnerability gives permission to other applications to send malicious intent to the application. Acting on receipt of intent without validating the caller's identity may lead to sensitive data being revealed or to denial of service.
SQLC_PASSWORD
This App uses SQL Cipher. But the secret may be hardcoded.
IMPLICIT-INTENT
A malicious activity or service can intercept an implicit intent and be started instead of the intended activity or service. This could result in the interception of data or in a denial of service.
BROADCAST-SERVICE
The vulnerability gives permission to other applications the power to start or bind the application's service. Using the flaw can lead to sensitive information leakage towards malicious apps or result in denial of service.
D_JSENABLED
Insecure WebView Implementation. Execution of user controlled code in WebView is a critical Security Hole.
D_EXTSTORAGE
App can read/write to External Storage. Any App can read data written to External Storage.
D_WEBVIEWDEBUG
Remote WebView debugging is enabled.
HANDLESSLERROR
You might also be interested in:
- Pradeo Security Mobile Threat Defense
- Pradeo Security Mobile Application Security Testing
- Pradeo Security In-App Self-Protection

.png)


