Smartphones and tablets have become the first point of access to the internet. This evolution has led to the creation of many Wi-Fi networks so people can connect from almost anywhere, but it opens a new playground for hackers. The growing amount of public networks and users who get connected to them has increased Man-In-The-Middle attack opportunities.
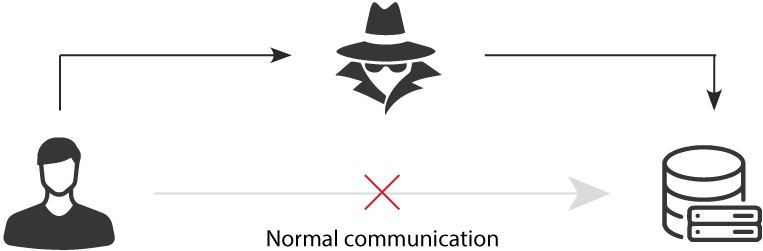
A Man-In-The-Middle attack, also known under the acronym MITM, happens when a communication between two parties is intercepted by an outside entity. The perpetrator either eavesdrops on the communication or impersonates one of the two parties, making it appear as a regular exchange of data.
A Man in The Middle cyberattack targets users of business email accounts, financial applications, e-commerce websites in order to steal their account details, credentials, bank account or credit card numbers. The final purpose is to perform identity theft, illicit money transfers or password modifications.
HOW A MAN IN THE MIDDLE ATTACK WORKS
Most of the time, the communication between two parties is intercepted through a Wi-Fi hotspot connection. Hackers create free-access hotspots using legitimate names and make them available to the public. Once a user connects its device to the malicious hotspot, any online data exchange is intercepted by the hacker.
In some other cases, hackers use IP, ARP or DNS spoofing techniques to display their website instead of the original one expected by the user. To do so, they hide their identity behind a trusted IP address (IP Spoofing) or they answer ARP or DNS requests with their own malicious IP address (ARP/DNS spoofing). This type of MITM attack mostly target financial websites.
WHAT A MAN IN THE MIDDLE ATTACK LEADS TO
Once a hacker is in position to intercept data, he can choose either to spy on communications or to tamper with them, for different purposes:
- Data and identity theft: A Man-In-The-Middle attack gives the hacker an access to accounts’ login credentials. Once holding these details, he can access sensitive business data (contacts, clients list, contracts…), accounts’ details and steal them.
- Illicit fund transfer: Hackers often intercept business email account credentials in order to access employees’ emails and spy on their content to spot an opportunity. For example, if a client is asking to an employee to send him the company’s banking details to make a payment, the hacker can usurp that employee’s email account and send then his own banking details instead of the company’s ones. So the client will transfer money to the attacker’s banking account. The hacker can also retrieve the banking application credentials, connect to the users’ accounts and transfer funds.
HOW TO PROTECT EMPLOYEES FROM MITM ATTACKS
First, employees should be aware of two basic security guidelines:
- Do not connect to public Wi-Fi hotspots (the ones not requiring any login are the riskiest), especially if you are planning on accessing sensitive data, making a fund transfer or accessing a business email account.
- Automatically check certificate authenticity provided by your browser and close any website that is flagged as unsafe or fraudulent.
Secondly, companies should define a security policy in alignment with their data criticality level and use a Mobile Threat Defense solution to enforce it. Using a MTD solution allows addressing network, OS and App security threats, while monitoring employees’ devices compliancy with the company’ security policy.
- Discover PRADEO SECURITY Mobile Threat Defense solution
- Download our Mobile Security Report 2018


-1.png)
.png)
-2.png)

