The largest online retailers in the world offer their products through mobile applications that are used by billions of customers. As a result, nowadays 82% of internet users shop online through their mobile device, according to a Statista report.
When a mobile application handles personal and financial data, it is required by data privacy laws, such as the General Data Protection Regulation (GDPR) and the Payment Service Directive 2 (PSD2), to embed security capabilities that’ll enforce privacy by design and prevent data breach.
The Pradeo Lab looked into Google Play’s 38 most downloaded shopping apps, shredding them with its app security testing tool. The results show they overly process personal data and handle them in a poorly secure manner.
Critical data transmitted through unsecure connections
Shopping applications handle users’ credit card details for obvious purposes. But it appears they also collect personal data such as contact lists, audio and video recordings and call logs for less clear reasons. Worst even, the way they process these sensitive data is clearly unsafe.
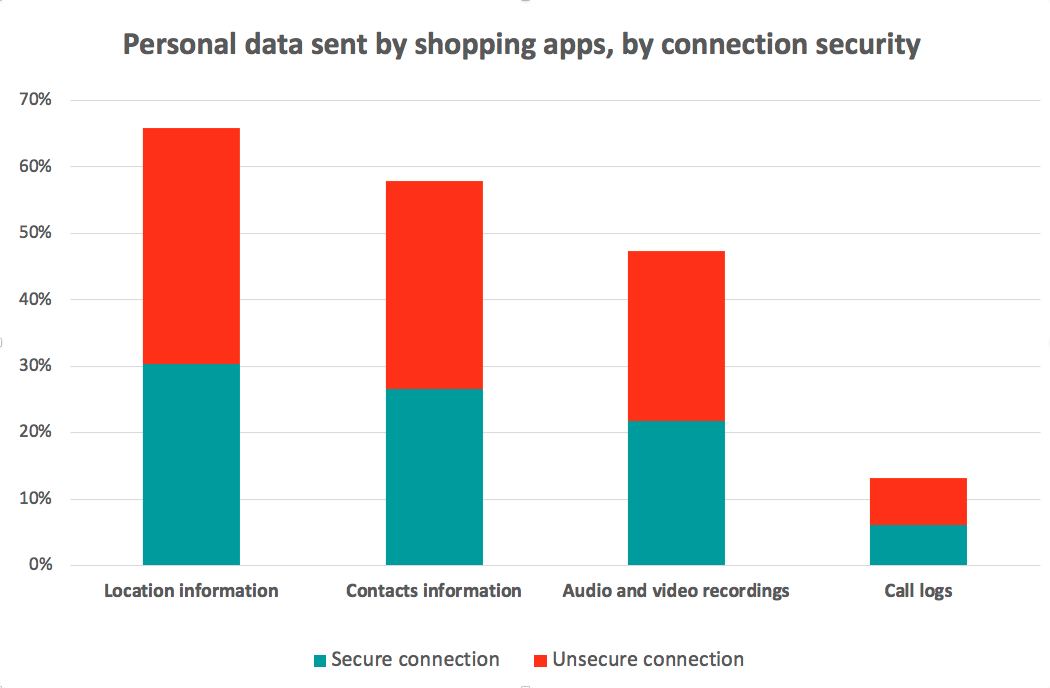
The graph below shows that shopping apps collect and send over the network users’ location information (66%), contact list (58%), audio and video recordings (47%) and call logs (13%). Besides, it highlights the repartition of personal data sent over the network, through secure connections (HTTPS with trusted certificate) or unsecure connections (HTTP or untrusted certificate).
Code vulnerabilities strongly endangering data privacy
The most used shopping mobile applications have an average of 13 code vulnerabilities per app. Here are the most severe vulnerabilities discovered, ranked by severity, with the percentage of apps featuring them.
- X509TrustManager: 53%
Unsafe implementation of the interface X509TrustManager. Specifically, the implementation ignores all SSL certificate validation errors when establishing an HTTPS connection to a remote host, thereby making the app vulnerable to man-in-the-middle attacks. - HandleSslError: 21%
The implementation ignores all SSL certificate validation errors, making the app vulnerable to man-in-the-middle attacks. - PotentiallyByPassSslConnection: 21%
The implementation bypasses all SSL certificate validation errors when establishing an HTTPS connection to a remote host, thereby making the app vulnerable to man-in-the-middle attacks. - URLCanonicalisation: 16%
The use of this method makes it easier for another application to access the application data. Depending on the implementation of Content Provider, it can lead to a directory traversal vulnerability. - World-Writable 8%
A file is World Writable. Any app can write in the file. - Implicit-Intent: 87%
A malicious activity or service can intercept an implicit intent and be started instead of the intended activity or service. This could result in the interception of data or in a denial of service. - Log: 47,4%
Log are readable. As they may include sensitive information, this vulnerability might lead to data leakage.Broadcast-Activity: 89% -
The vulnerability gives permission to other applications to bypass some security access, providing direct access to potentially sensitive data.
Broadcast-Service: 90% -
The vulnerability gives permission to other applications to start or bind the application's service. It can lead to sensitive information leakage or result in denial of service.
- Broadcast-Receiver: 84%
The vulnerability gives permission to other applications to send malicious intent to the application. Not validating the caller's identity may lead to sensitive data being revealed or to denial of service.
The full anonymized app security report is available to the press on-demand.
It includes for each app:
- The list of personal data sent over the network
- The list of device information sent over the network
- The amount of http / https connections
- The amount of uncertified connections
- The amount and detail of code vulnerabilities
- The amount of embedded third-party libraries
You might be interested in:

.png)


