This year may mark a turning point in the cyber world. As the pandemic urged organizations to enable remote working, the dissolution of traditional security perimeters accelerated until they fully blew apart. People with bad intentions saw in this chaos an opportunity to spy on an opponent, a government, a competitor; or to steal companies, public institutions, individuals…
A recent research conducted by NFU Mutual highlights that 47% of organizations feel more vulnerable to cyberattacks since the increase of remote working, but 45% of them have not yet taken any action to protect themselves from cybercrime. The number of data breaches that occurred in the last months confirm that statement. Reshaping security strategies is the only way to fully cover the new extended attack surface to slow the trend. Here are a few facts to be aware of.
Mobile phishing is booming
Phishing campaigns can serve two purposes. Stealing credentials, or have users install a malicious application. In both cases, they have shown to be increasingly sophisticated and a lot of mobile users are still unaware of their existence, hence easily falling in the trap.
To steal credential
A recent research lead by Pradeo in Q4 2020 shows that 34% of employees click on the link showcased in phishing attempts sent by text message (email, SMS or through messaging apps), and overall, 19% go through by providing their credentials. As phishing is undeniably effective, the dark web is flourishing with hackers selling credential databases.
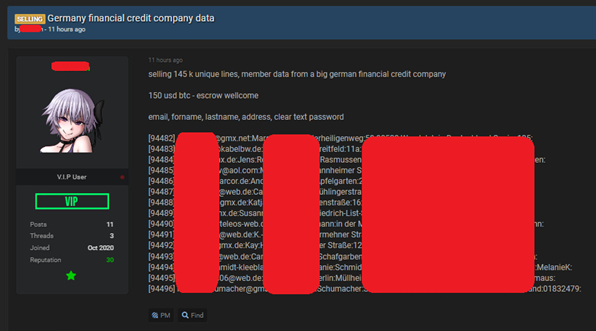
Source: https://twitter.com/Bank_Security
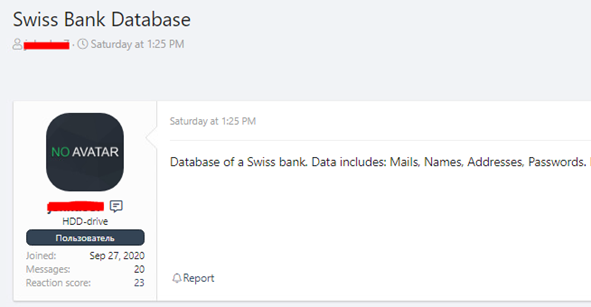
Source: https://twitter.com/Bank_Security
To deliver malware
Beginning of December, a massive phishing campaign occurred in France through SMS (smishing). The text message impersonated the French government and encouraged to download the Covid tracking app “Tousanticovid”, through a specified link. The app in question was in fact a malicious clone that mimicked the official app and was stuffed with malicious hidden behaviors, programmed to steal users’ data and credentials.
Public and defense organizations are highly targeted
Since January, announcements of data breaches occurring in the public sector have been nearly continuous. Defense, health, administration, and education organizations were repeatedly hit globally. Here are some of them:
Defense
- Cybersecurity firm Fireye hacked by suspected nation-state, and fraudsters were after US government agencies data.
- China suspected of spying on Americans via Caribbean phone networks.
- The Defense Information Systems Agency (DISA), which handles IT for the White House, admitted to a data breach potentially compromising employee records.
- The Illinois Department of Employment Security (IDES) leaked records concerning citizens applying for unemployment benefits.
- The United Nations International Maritime Organization (UN IMO) disclosed a security breach affecting public systems.
Health
- In Germany, a hospital patient died after being redirected away from a hospital suffering an active ransomware attack.
- Pfizer/BioNTech vaccine files have been hacked from the European Medicines Agency.
Administration
- The taxpayer identification numbers of 1.26 million Danish citizens were exposed by Denmark's government tax portal.
- In Vancouver, a ransomware attack disrupted Compass metro cards and Compass ticketing kiosks for two days.
Education
- The Manor Independent School District in Texas lost $2.3 million during a phishing scam.
- The University of California SF paid a $1.14 million ransom to hackers in order to save COVID-19 research.
- The UK University of York disclosed a data breach caused by Blackbaud. Staff and student records were stolen.
- A Nevada school, suffering a ransomware attack, refused to pay the cybercriminals -- and so student data were published online in retaliation.
Mobile malwares are turning into swiss knives
There are plenty of malwares, and each has its own purpose: a keylogger records keyboard strokes, a One-Time-Password interceptor hijacks incoming SMS or authenticator apps, a spyware collects and sends user’s data over the network, and so on. This year, Pradeo’s researchers observed a switch in the way malwares achieve their hack. To be more efficient, they now combine several attack techniques.
The new strain of Android malware named Alien is the perfect example of this increasing sophistication. Alien is promoted as a Malware-as-a-Service on dark web’s forums. It comes with a set of features allowing it to clone more than 200 applications to phish credentials, steal contact lists and SMS, log keystrokes, lock the screen, etc.
Such mobile malwares evolve so quickly that they cannot be detected by antivirus, as they have no viral signature, and cannot be addressed with EDR solutions as they require real-time detection and blocking. Only behavioral analysis and automatic remediation on the mobile device can fight them off.


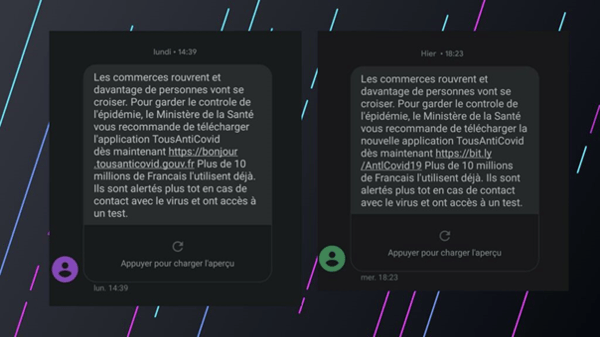

-1.png)
-1.png)
.png)

