We detected yesterday on Google Play a malicious mobile application with 10K+ installs called “Daily Food Diary”. The cybercriminal who published this app bypassed Play Protect security by deeply obfuscating its malicious code. After being reported, the malware was shortly deleted from the official store this morning. Users are advised to promptly uninstall it from their devices.
Package: com.dailyapp.fooddiary
Version: 22
Installs: 10,000+
Daily Food Diary is pretending to be a legitimate app in which you can take pictures of your meals and set mealtime alerts. It features a very minimal design and a few basic functionalities with no real purpose. In fact, the app true nature is malicious.
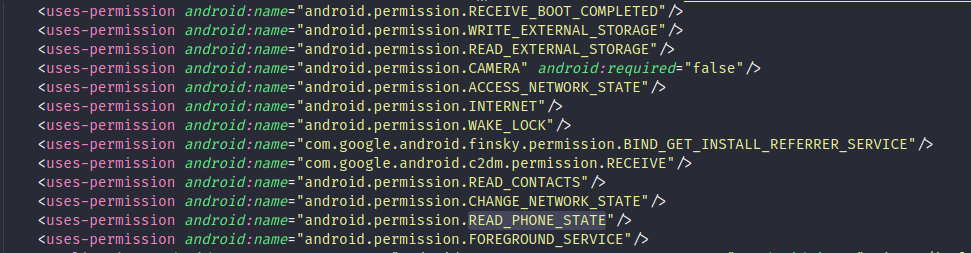
When users launch it, they are immediately sent to the device settings to enable the app to automatically run at startup (foreground service permission). Besides, the app is set to always run in the background (wake lock permission). When users are on the app interface, attempts to exit are overridden to make it difficult to close it.
Daily Food Diary repeatedly asks for permissions to access the contact list, and when it gets it, it directly exfiltrates contacts' information to an unknown external storage. It also requests to manage phone calls, to potentially refuse incoming calls that would temporarily prevent the app from running in the background. Other lines of code seem to be related to the Joker malware.
A sophisticated mix of obfuscation and encryption
To hide its true intentions, Daily Food Diary malicious code is hidden in an encrypted file called 0OO00l111l1l. Other files contain the native library that can decrypt the malicious code so it can execute (libshellx-super.2019.so), the encryption key (tosversion) and additional resources (o0oooOO0ooOo.dat).
Besides, to stay undetected from dynamic analysis, the app does not perform its malicious behaviors when running in an emulator.
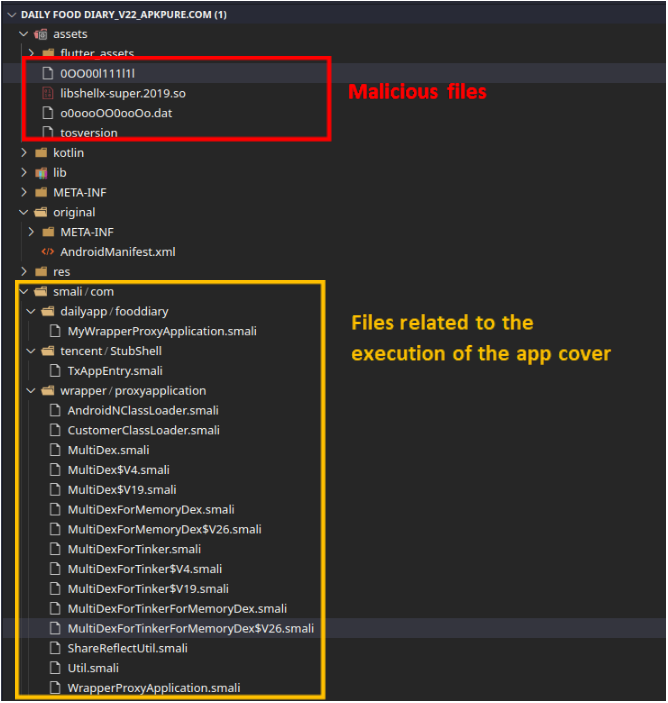
TOSversion :

Permissions :


.png)


