In 2023, 63% of companies were victims of ransomware, according to Sophos.. At a time when we hear more often than ever about this threat in the global media, it should be noted that ransomwares are not new, but currently gaining a lot of popularity among cybercriminals.
Today, a wide variety of public and private organizations are attacked. However, for cybercriminals the most suitable targets are those with poor IT hygiene, in fruitful sectors or whose activity continuance is critical. Quite often, public organizations' cyberdefense budgets are not adapted to the criticality of the information they handle. Thus, they are particularly affected by threats such as ransomwares.
When the criticality of some devices is underestimated, as it is often the case with smartphones and tablets, hackers' access is facilitated.
Evolution of ransomwares
Two new trends have emerged. On the one hand, it has been observed that ransomwares are often used as part of large-scale attacks, sometimes prepared months in advance and targeting carefully selected companies or public institutions (critical sector, high added value...). Qualified as Big Game Hunting, these onslaughts are often carried out by teams of hackers who have more financial and/or human resources than the average.
The second trend is the opposite of the first. It is the widespread of Ransomware-as-a-Service offers on the dark web, aimed at people with little IT knowledge and looking for a simple and fast way to launch attacks. The Jigsaw ransomware, for example, is sold for about 3,000 dollars on cybercriminal forums. RaaS is available on a subscription basis and sometimes offers a management platform like any SaaS solution to monitor attacks. Much less powerful than Big Game Hunting, RaaS usually targets individuals or small businesses, randomly.
How can a ransomware infiltrate your system?
Infection methodology
To deploy a ransomware on an organization's information system, cybercriminals use fleets of computers, smartphones or tablets. Often, they use phishing and software vulnerabilities.
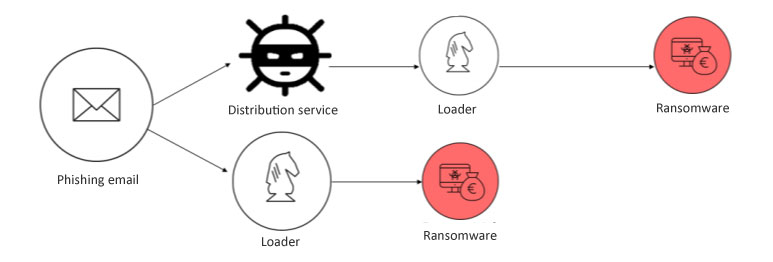
Phishing email
Operable on a large scale for free, email is a favoured way to spread ransomwares. A study conducted by Pradeo shows that 34% of employees click on the link presented in phishing attempts sent by text message (email, SMS or via messaging applications).
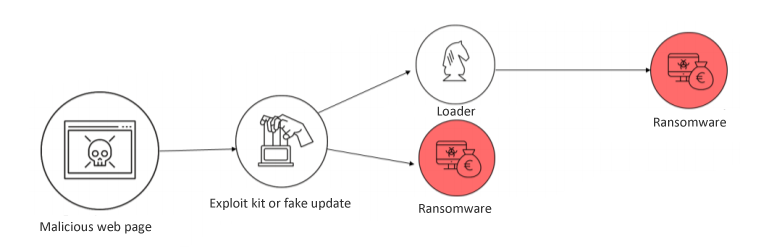
Malicious or hijacked web page
Some websites mimic known company pages or display a false window to entice Internet users to download a program, for example, claiming a security flaw in the OS or a required update. The program is actually a malware.
Vulnerabilities exploitation
- Server: Some network vulnerabilities can be exploited to spread malware. A week ago, the banking system in India fell victim to it.
- Software: Security holes in softwares can facilitate access to corporate data. For example, the democratization of VPN services makes them a target of choice and some are victims of brute force attacks to obtain administrators' credentials.
Encryption and ransom demand
When installed on a device connected to an information system, ransomwares quarantine security and remote management programs, and then encrypt local and remote files, connected disks, etc. Once this step is completed, a ransom is asked.
In most cases, hackers demand to be contacted within a given time frame. Beyond that deadline, the encrypted information is erased, sold or published online.
However, even if the payment is made (often in cryptocurrency, therefore untraceable), the organization is not sure to recover all of its data. To have an order of magnitude, the amount of a ransom ranges from a few thousand euros for an individual, and varies between 200,000 and 10 million dollars for the DarkSide and WastedLocker ransomwares.
Heavy consequences
Financial losses
Ransomwares are intended to extort money. When they are trapped, organizations face a dilemma: should we pay the ransom? Whatever their answer is, they will have to face financial losses related to an untimely shutdown of their activity, a complete clean-up of their information system, investigations to establish the source of the attack, penalties from data protection authorities, etc...
Data leaks
During a ransomware attack and regardless of the reaction of the victim, data leakage is inevitable. Even when the ransom is paid and the data is restored, the stolen information usually ends up on the black market.
Forced shutdown
A cyberattack often renders the computer system inoperable. It can slow down or even paralyze the activity of the affected organization. In some sectors, this leads to considerable financial losses, in others, such as in the healthcare sector and particularly in hospitals, it directly jeopardizes patients' safety.
Image damages
When an organization falls victim to ransomware, or any other attack leading to data leakage, it is difficult to keep it quiet. Sometimes, the legislation requires (in most countries) to notify such incidents to the government agency in charge of data protection. The media coverage of a security breach has serious consequences on a brand image, which can cause a loss of confidence from stakeholders: customers, partners, investors, etc.
Prevent ransomware from exploiting your mobile fleet to infect your information system, protect your mobile devices with Pradeo Security.




