The arising of Android 10 major release and consequently Android Enterprise brings plethora of questions around how to manage and secure Android devices.
If Android Enterprise smoothen the administration of devices, it does not add a structuring piece to Unified Endpoint Management security.
This article aims at clarifying the ins and outs underlying Android Enterprise and the key security steps to be implemented to ensure Android devices security.
The homogenization of device management
The number one goal of Android Enterprise is to deliver a common set of device management APIs in order to ensure a reliable Enterprise Mobility Management (EMM) experience.
The openness of the Android system led manufacturers to implement their own set of APIs over the years and ultimately brought inconsistency with regards to device management.
Through the Android Enterprise program, Google decided to close the gap and strengthen the foundations of device management across devices embedding the OS.
The separation between work and personal profiles
Android Enterprise comes along with the objective of separating work and personal data to accompany ever-growing BYOD usages.
One of the 4 setup mode below needs to be chosen when enabling Android Enterprise through the management solution.
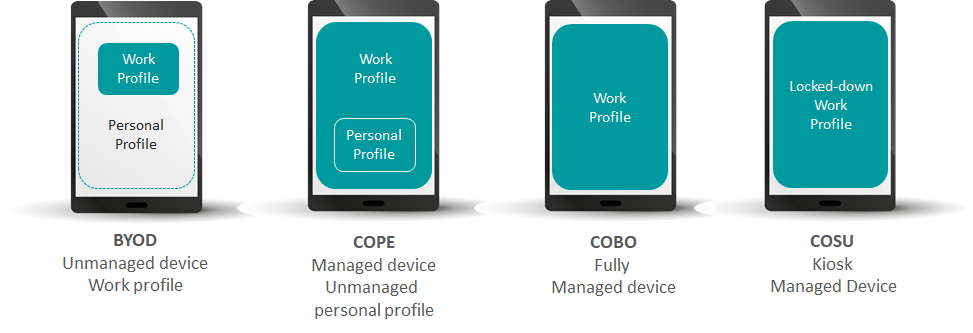
By defining the mode of usage, companies can have a full or a restricted visibility on devices and ensure collaborators of their privacy in a BYOD context. Factually, this notion reproduces and extends containerization capability already provided by EMM tools. Therefore the same security assessment applies:
- Existing EMM security capabilities aim at enforcing security measures (wipe a device, lock down the work profile, black list a given application) and not perform on-device threat detection and remediation.
- Even if the work profile is encrypted, the personal environment can jeopardize corporate security through malicious or leaky applications (screenlogger, contacts leakages, …), device improper settings (rooted or jailbroken, outdated OS, …), …
As a result, Mobile Threat Defense still remain a centerpiece of the Android Enterprise security puzzle to provide a behavioral analysis of the mobile context and dynamically trigger preventive actions.
Pradeo Security Mobile Threat Defense comes as two complementary deployment modes:
- Agentless app vetting through a one-click platform to platform integration. More in our Mobile Threat Defense Easy Connect datasheet.
- 360° on-device protection delivering application, network and device threat defense as well as real-time remediation. More in our Mobile Threat Defense datasheet.
A managed store
Ultimately, Android Enterprise offers a portal containing apps approved by the company and to be distributed onto users' work profile. It reflects legacy Mobile Application Management feature provided by EMM solutions. Some providers are leveraging the managed Google Play and some others are still maintaining their own app catalog.
Relying on the Google managed store does not leverage any security checks against the company policy. Thus, the vetting of applications remains a security pre-requisite before any publication on both the managed Google store or the EMM app catalog.
The Pradeo Security engine leveraged in Pradeo’s Mobile Application Security Testing service has been analyzing mobile applications for nearly 10 years, constantly improving its detection capability to keep its unparalleled level of accuracy. Here is why IDC acknowledged Pradeo as a clear leader of the MAST market.



-1.png)
-1.png)
.png)

