Mobile apps are now on top of our digital consumption and they process data from millions of users all around the globe every day. The growing request of renewal and immediacy pushes organizations to create applications at a very fast pace, leaving behind the security tests.
A mobile application can contain two types of vulnerabilities:
- Unwanted behaviors: Unexpected actions are done by doing useless background activities.
- Vulnerabilities: It can contain vulnerabilities exposing it to attacks.
To help developers create and maintain safe mobile apps, the OWASP organization classified a large amount of mobile applications vulnerabilities in their “OWASP Mobile Security Project”.
Pradeo’s behavioral analysis engine factors OWASP vulnerabilities in, among hundreds of others, and detects their presence in every app it analyses. On a representative sample of 2 million applications tested on our platform, Pradeo’s research team found out that almost one-third of them contain an OWASP vulnerability.
Theses vulnerabilities are listed in four categories:
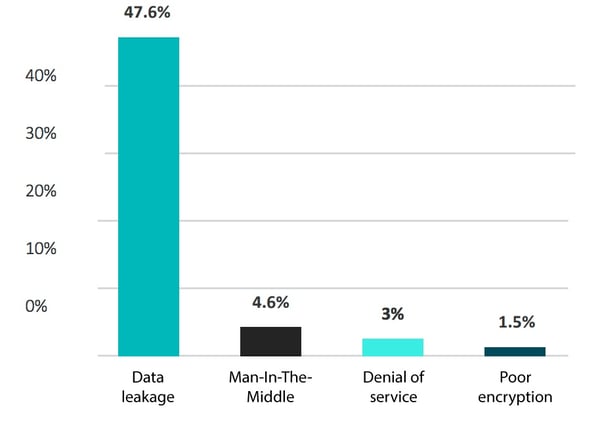
Data leakage
Among the vulnerabilities detected in the analyzed applications, 47% can lead to data leakage. Data disclosure became in the last few years the main threat that companies need to face.
Example of vulnerabilities in the realm of this category:
- Broadcast-Activity: This vulnerability manifest when the application’s ‘Activity’ component hasn’t a high enough protection level. It allows the third-party app to avoid some security measures to access sensitive data.
- Broadcast-Service: This vulnerability manifest when the application’s ‘Service’ component hasn’t a high enough protection level. It allows the third-party app to launch or to link itself to the service.
- Implicit-Intent: Every data broadcasted through this method is prone to be caught by a third-party app.
Man-In-The-Middle-Attack (MITM)
A Man-In-The-Middle attack happens when a communication between two parties is intercepted by an outside entity. The perpetrator either eavesdrops on the communication or impersonates one of the two parties, making it appear as a regular exchange of data. 4.6% of applications tested contain vulnerabilities that can lead to this type of attack, exposing users to fund theft, data theft or their IoT objects takeover.
Example of vulnerabilities in the realm of this category:
- 509TrustManager: This vulnerability manifest when the interface X.509TrustManager is implemented in an unsafe way, which ignores all SSL certificate validation errors when it connects in HTTPS to a remote host.
- HandleSslError: Every validation error message from the SSL certificate is ignored, which authorizes invalid certificate.
- PotentiallyByPassSslConnection: This vulnerability corresponds of the unsafe implementation, which ignores all SSL certificate validation errors when it connects in HTTPS to a remote host.
Denial of service attack (DoS)
A denial-of-service (DoS) is any type of attack where the attackers attempt to prevent legitimate users from accessing the service. In a DoS attack, the attacker usually sends excessive messages asking the network or server to authenticate requests that have invalid return addresses.
Among the sample of apps, 3% contain vulnerabilities to this type of attacks, putting at risk the availability of their services.
Example of vulnerabilities in the realm of this category:
- URLCanonicalisation: Depending on the ‘ContentProvider’ utilization, this method use can lead to a directory crossing vulnerability.
- MaliciousIntents: A third-party malicious app can send an ‘intent’ to an app component that shouldn’t be allowed to receive it.
Poor encryption
Cryptography techniques aim at making some data illegible to ensure their security. 1.5% of the tested apps showed encryption weaknesses, leaving a breach towards sensitive data.
Example of vulnerabilities in the realm of this category:
- AES: Encryption method AES doesn’t ensure data confidentiality, integrity and authenticity.
- ECB: The app uses the ECB mode in its encryption algorithm. The ECB mode is known for being weak, because it uses the same encoded text for identical plain texts blocs.



-2.png)
-3.png)
.png)

