The current resurgence of the Pegasus spyware is shedding light on a fundamental problematic raised for years by mobile devices: How private mobile data can be?
The Pegasus Project revealed in July 2021 that 50.000 people have been directly hit by the spyware, but the stolen information also involve everyone connected to the victims. Sometimes, it is just easier to reach a target through its network, and that’s also what Pegasus does.
In February 2024, the detection of the Pegasus spyware in the phones of two European parliamentarians, as well as in that of a European Parliament staff member, has brought the threat back into focus:
"My phone has been infected by the Pegasus spyware."
Nathalie Loiseau - Chair of the Subcommittee on Security and Defense of the European Parliament
While Android and iOS operating systems are developed taking mobile security into account, with such a spyware, the NSO group demonstrates that standard mobile OS safeguards are not reliable enough to keep users’ data safe, bringing to the fore the necessity to add an extra layer of security to all mobile devices.
Pradeo, global mobile security leader, is actively helping its users in fighting mobile data theft and leakage since 2010. Here is our analysis of the Pegasus spyware.
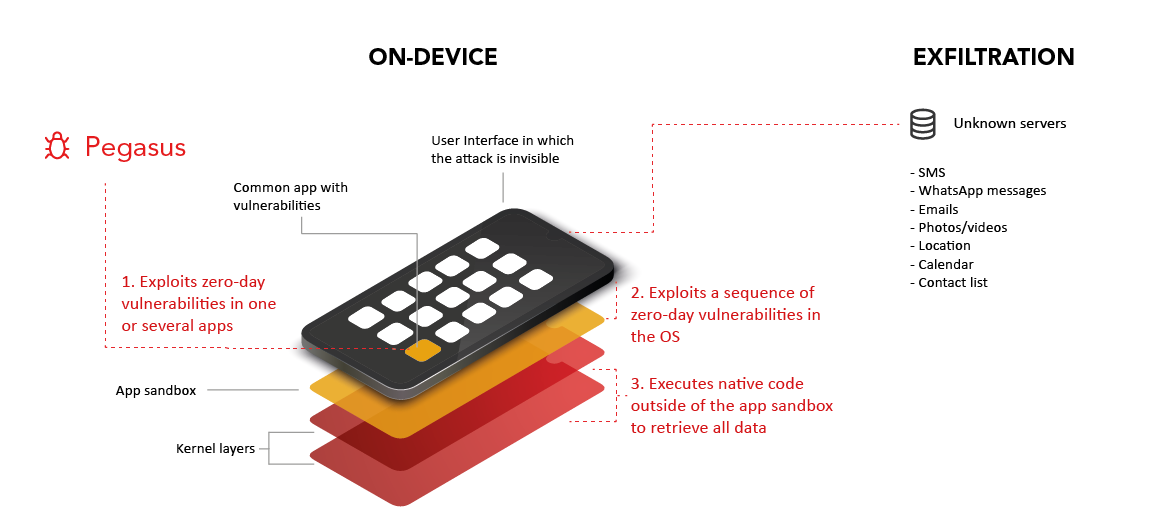
Pegasus, modus operandi
To compromise high-value targets, the Pegasus spyware exploits vulnerabilities in common apps such as iMessage, FaceTime, Safari, WhatsApp, etc. that have a web module (WebKit, WebView…) to silently reach invisible and unclassified dynamically generated URLs.
The reached pages then execute JavaScript code to exploit vulnerabilities to get out of the applications’ sandboxes, hence bypassing all mechanisms in place in the Android and iOS systems.
Once in the kernel layers, Pegasus exploits a sequence of zero-day and known processor vulnerabilities to execute arbitrary code (Arbitrary Code Execution) without requiring the system to be rooted or jailbroken. The code is charged directly into the RAM and not as an application, making it tricky to be detected. After achieving all these steps, Pegasus massively exfiltrates users’ data, including encrypted ones (WhatsApp, Signal, Telegram conversations...).
What to learn from Pegasus
Mobile devices are undeniable high-value targets
In 10 years, the smartphone became the connected device that is the most used for both professional and personal usages. Always close to hand, it accesses and stores almost every single data related to an individual: agenda, locations, contacts, photos, conversations… Still, at a time when data protection is increasingly enforced, cybersecurity practices in place do not measure up with the sensitiveness of those devices.
Recently, we have witnessed a surge in cyberattacks with more and more headlines pointing towards mobile-originated breaches. Pegasus brings the reality of the multi-level fallibility of a mobile device and the broad reach of a mobile attack.
A mobile device can be compromised at the application, the network and the OS level. For 76% of mobile data breaches, applications are involved. On average, 3 apps out of 5 have vulnerabilities and/or backdoors that can be exploited to exfiltrate data. Aside from apps, network connections (cellular, WiFi, BlueTooth, NFC…) represent another direct access point to data transiting from the mobile devices over the network, exposing them to eavesdropping or infecting them with incoming malicious code. And finally, OS misconfigurations and vulnerabilities can be exploited to escalate privilege and access users’ data that are stored on the device. Pegasus acts at each of these levels to spy on its victims.
iOS is not an impregnable fortress
Until now, the common belief was that the lockdown approach inherent to the iOS system made it invulnerable to cyberattacks. The Pegasus Project definitively turned down this urban myth with, among other cases, an iPhone 12 Pro Max running the latest version of the system 14.6 being compromised by a zero-click attack through an iMessage zero-day vulnerability exploit in June 2021.
“When we’re talking about something like an iPhone, they’re all running the same software around the world. So if they find a way to hack one iPhone, they’ve found a way to hack all of them.” Commented Edward Snowden.
Despite considerable efforts initiated by Apple, iOS is fallible just like any system and the fact that most devices are simultaneously running on the same version has its downside. The cyberthreat landscape is continuously evolving and breaking into the Apple system is an exciting and lucrative activity for hackers.
Largescale surveillance is not a new story
Pegasus highlights the depth of a largescale attack targeting head of states, political figures, or journalists. However, it should not elude that surveillance is performed on a daily basis through industry-oriented approaches, non-targeted data exfiltration hackings, and even common marketing practices. The dark web is chock-full of data brokers monetizing 1 million active users’ data for an average of 4000 USD/month.
Therefore, every single mobile user and all companies should be concerned about how data are handled on mobile devices and what measures are in place to prevent data exfiltration.



-1.png)
-1.png)
-1.png)

