This article is regularly updated with the names of new mobile applications infected with Joker malware but yet available for download on Google Play. Our team always alerts Google of its discoveries.
Updated on Tuesday July 5th, 2022
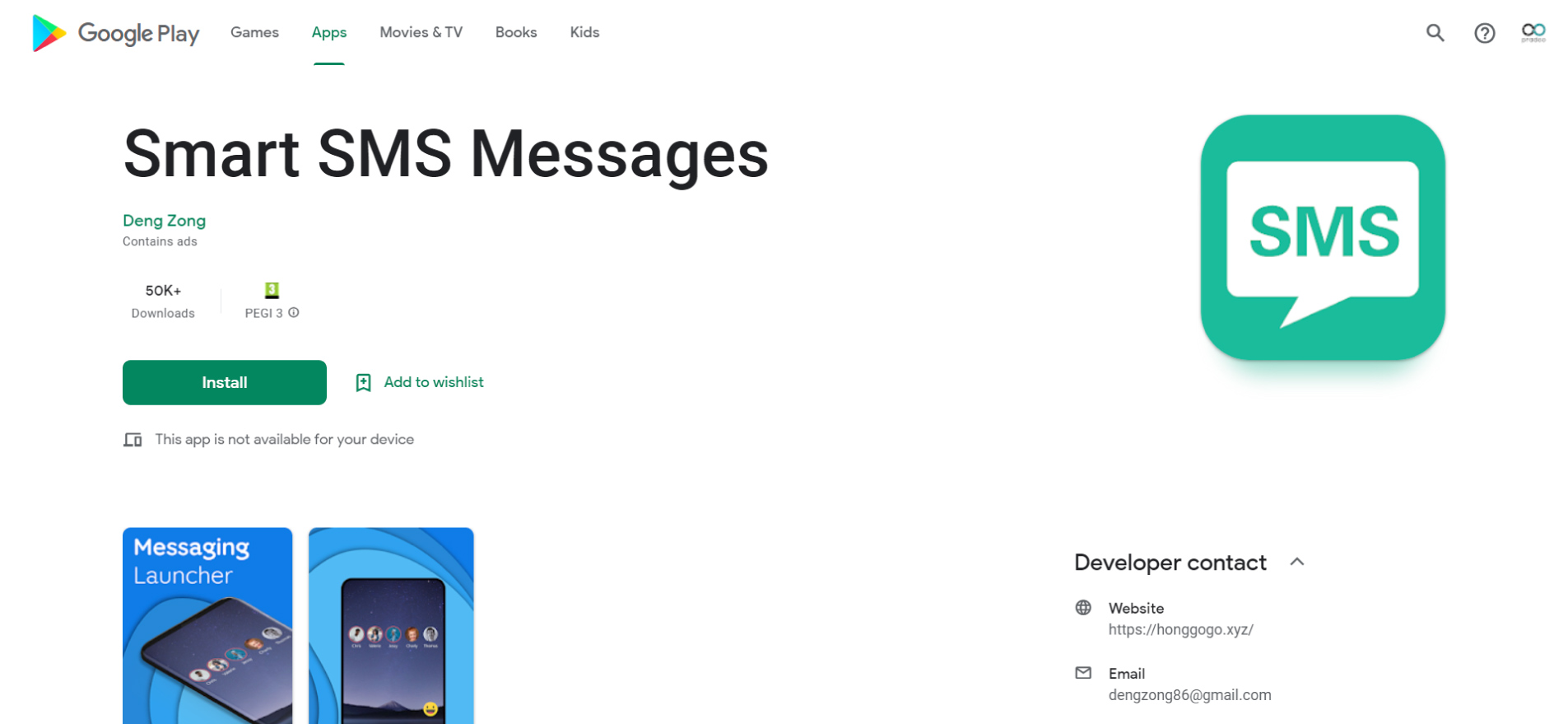
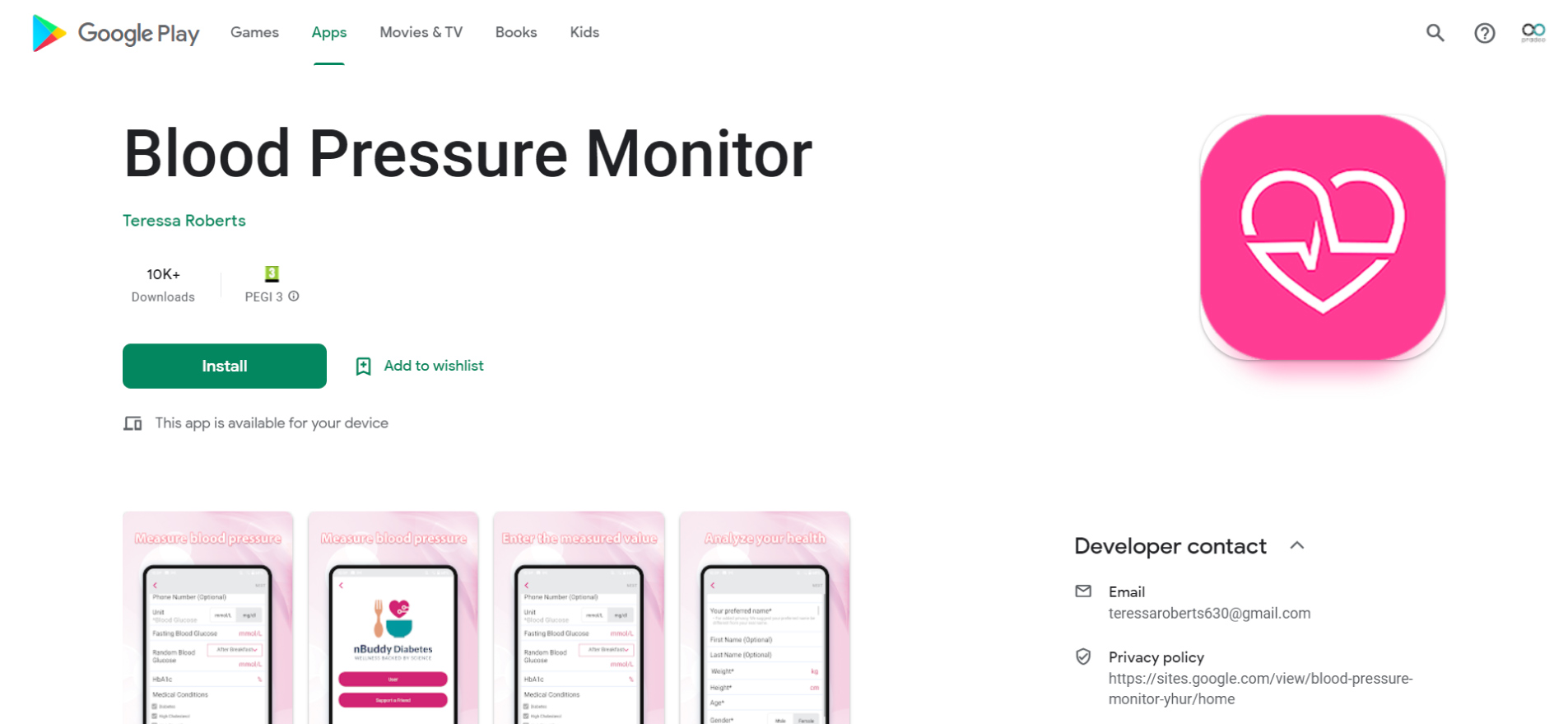
Pradeo just identified 4 new malicious applications embedding the Joker malware and acting as droppers, available for download on Google Play. Jointly, they have been installed by 100.000+ users.
Joker is categorized as Fleeceware, as its main activity is to subscribe to unwanted paid services or send SMS / make calls to premium numbers, unbeknownst to users. By using as little code as possible and thoroughly hiding it, Joker generates a very discreet footprint that can be tricky to detect. In the last three years, the malware was found hiding in thousands of apps.
Users are advised to immediately delete these applications from their smartphones and tablets to avoid fraudulent activities:
How it works
Our analysis of the above-mentioned applications shows that they use various mechanism to commit fraud, through in-app purchase or SMS sending to premium numbers.
To bypass two-factor authentication protocols during in-app purchases, Smart SMS Messages and Blood Pressure monitor intercept one-time passwords. To do so, the first one simply reads SMS and takes silent screenshots, the second one intercepts notifications’ content. Victims only notice the fraud when receiving their mobile phone invoice, potentially weeks after it started.
All of these apps are programmed to install other applications on users’ devices, acting as dropper to potentially convey even more dangerous malware.
By diving into these applications, we noticed several elements that compose a pattern when it comes to malicious applications on Google Play, and that could help users anticipate their malicious nature. First, their developers’ account only feature one app each. Usually once they are banned from the store, they simply create another one. Secondly, their privacy policies are short, use a template, never disclose the full extent of the activities the apps can perform and are hosted on a Google Doc or Google Site page. Finally, those applications are never related to a company name or website.
Previously infected applications
Beautiful Themed Keyboard
Package: com.expression.kept.current.keyboardthemes
Version: 3.6
Installs: 5.000+
All Wallpaper Messenger
Package: com.estarpro.liteSMS
Version: 2.2.0
Installs: 100.000+
Angina Reports
Package: com.anbackward.reportsanginahealthy
Version: 1.05.20
Installs: 5.000+
Moon Horoscope
Package: com.hearite.moonhoroscope
Version: 51.5
Installs: 10.000+
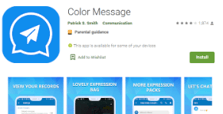
Color Message
Package: com.guo.smscolor.amessage
Version: 3.1
Installs: 100.000+
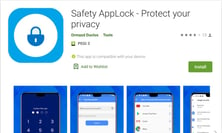
Safety AppLock
Package: applock.safety.protect.apps
Version: 6.5
Installs: 10.000+
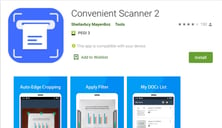
Convenient Scanner 2
Package: com.convenient.scanner.tb
Version: 14.0.4
Installs: 100.000+
Push Message-Texting&SMS
Package: sms.pushmessage.messaging
Version: 4.13
Installs: 10.000+
Emoji Wallpaper
Package: tw.hdwallpaperthemes.emoji.wallpaper
Version: 14.3
Installs: 10.000+
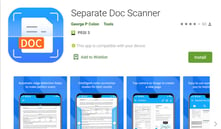
Separate Doc Scanner
Package: sk.pdf.separatedoc.scanner
Version: 2.0.74
Installs: 50.000+
Fingertip GameBox
Package: com.theone.finger.games
Version: 3.0.7
Installs: 1000+
For more information, write to roxane.suau@pradeo.com.





.png)


