Mobile devices represent the fastest growing attack surface and the widespread use of remote working has been accelerating it lately. Cybercriminals target enterprises through collaborators’ smartphones and tablets, betting on finding loopholes they will exploit to steal corporate data. Security heads are looking to extend their Zero Trust IT security strategy to mobile devices and apps, but the versatility of mobility makes it challenging.
The Zero Trust model is a security approach based on the principle of not trusting any network or data access request by default, and to secure all entry points. It has emerged as the most reliable way for companies to keep away cyberthreats evolving within their distant and immediate environment.
Top threats countered by Pradeo in 2020
In 2020, Pradeo’s engine has analyzed billions of mobile security events related to data exfiltration, malwares (banking trojans, screenloggers…) network attacks, system exploits, etc. Even through threats compromising mobile devices leverage various entry points, mobile applications remain cybercriminals’ favored vector to spy and steal data. The network comes second and gains ground in correlation with the growing number of connections to unsecure free WiFi globally.
- Ransomwares are now found in 1.1% of mobile apps, against 0.01% a year ago (+10900%).
- 7% of mobile apps hide a fleeceware.
- 66% of mobile apps exfiltrate users’ data (contacts, call logs…) through the network, legally but very often unbeknownst to users.
- 34% of employees are trapped by phishing attempts.
- Globally, Man-in-the-Middle attempts on mobile have grown by 236% in the last year.
- 95% of Android devices run on obsolete versions, versus 76% of iOS devices.
- All obsolete OS versions have many public CVEs: 1626 on average for iOS and 864 for Android.
Identification of your mobile framework and its vulnerabilities
Identify weak entry points to your information system
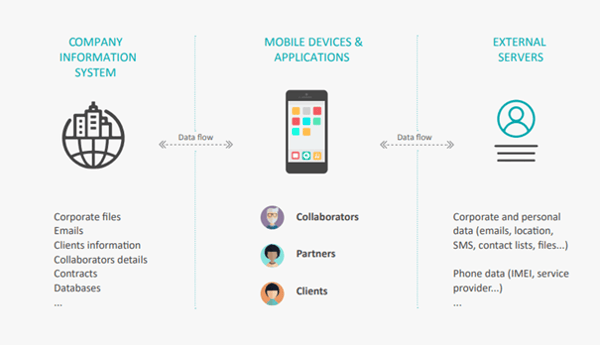
Mobility is vast and results in numerous data exchanges, making mobile frameworks sometimes difficult to visualize. The data mapping below represents all the flows potentially created by the usage of mobile devices and applications.
As a first step, organizations should define which parts of this mapping apply to their structure. Then, all the data handled need to be qualified. Information that are valuable to the company as well as the ones that fall under dedicated legislations need to be identified. For example, as personal data processing is strongly regulated by some laws like the General Data Protection Regulation, they require organizations to pay them a special attention, and the same applies for financial and health data.
Secondly, security heads can determine whether sensitive and valuable data are manipulated through their mobile framework and their degree of exposure to attack and leakage. Security measures will be considered accordingly.
Selection of solutions to prevent mobile data breach
Get visibility on data processing, leakage and theft within a mobile environment
Most security heads encounter difficulties qualifying and quantifying threats surrounding their mobile environment. Pradeo’s threat intelligence collector gathers mobile security events (data accessed, send over the network…) and attack logs from managed mobile devices (mobile fleet) or non-managed mobile devices (clients, partners…, entirely anonymously) and obtain visibility onto an existing threat landscape. Pradeo’s Mobile Application Security Testing online service reveals mobile apps’ actions on all data, with an emphasis on personal ones. Organizations like the Groupe Rocher rely on it to audit their mobile apps before releasing them.
Ensure the security of the data manipulated by mobile collaborators
Unified Endpoint Management vendors such as VMware Workspace ONE, IBM MaaS360, Microsoft Endpoint Manager, BlackBerry UEM, etc. promote threat detection and response integrations within their platforms to fully protect corporate data accessed by mobile devices. Pradeo Security Mobile Threat Defense technology allows identifying and blocking threats in real time on users’ devices and to automatically synchronize lists of uncompliant devices and applications on the UEM platform. It fully protects corporate data from malwares and exfiltration.
Deliver secure mobile services to non-managed devices
Sometimes, organizations choose not to equip their employees with mobile devices, preferring to allow them to bring their own device (BYOD). But collaborators using their personal smartphones for professional purpose may not allow their employer to enroll their device to manage them. Hence, they end up non-managed while accessing corporate data. To provide mobile services to collaborators using non-managed devices, Pradeo Security offers entirely secure private stores. The store enables organizations to distribute secure mobile services without having to manage a mobile fleet nor engaging internal development processes.
Ensure the security of data manipulated by a mobile app
Once distributed to the public, mobile applications (banking, health, retail…) run on non-managed devices that are potentially compromised or hosting malwares. Mobile applications need to be properly shielded to face threats coming from their execution environment, to keep safe the sensitive data they manipulate. Pradeo Security In-App Protection solutions (SDK) protects mobile applications from the inside out. Once integrated into an application, it diagnoses its environment, detects unwanted and malicious behaviors performed on the devices hosting the app and offers an automated and adapted security response.
The first key to successfully securing mobility is to accurately distinguish threats from legitimate behaviors, quickly and automatically. The second one lies in ensuring minimum footprints to maintain everyone’s agility. The Pradeo Security solution suite is recognized for its precision and ease-of-use.
For more details, contact us.



-1.png)
-1.png)
.png)

