This week, our engine detected two spyware hiding on the Google Play Store and affecting up to 1.5 million users. Both applications are from the same developer, pose as file management applications and feature similar malicious behaviors. They are programmed to launch without users’ interaction, and to silently exfiltrate sensitive users’ data towards various malicious servers based in China. We have alerted Google of the discovery before publishing this alert.
How to identify these spyware?
File Recovery and Data Recovery - com.spot.music.filedate - 1M+ Installs
File Manager - com.file.box.master.gkd - 500K+ Installs


Breached data: From contacts lists to all media…
On the Google Play Store, both the above-mentioned applications’ profiles announce that they do not collect any data from users’ devices, which we found to be false information. Furthermore, they announce that if data was collected, users could not request it to be deleted, which is against most data protection laws like the GDPR.
-1.png?width=444&height=221&name=MicrosoftTeams-image%20(2)-1.png)
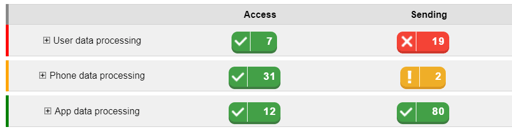
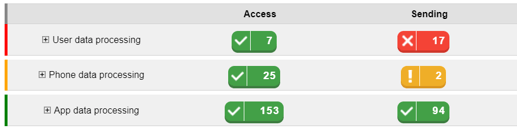
The reports from our behavioral analysis engine show that both spyware collect very personal data from their targets, to send them to a large number of destinations which are mostly located in China and identified as malicious. Stolen data include:
- Users’ contact lists from the device itself and from all connected accounts such as email, social networks…
- Media compiled in the application: Pictures, audio and video contents
- Real time user location
- Mobile country code
- Network provider name
- Network code of the SIM provider
- Operating system version number, which can lead to vulnerable system exploit like the Pegasus spyware did
- Device brand and model
Specifically, each application performs more than a hundred transmissions of the collected data, an amount that is so large it is rarely observed.
File Manager :
File Recovery and Data Recovery :
Sneaky behaviors used by the hacker to increase its success
- Looking legitimate: When navigating on application stores, we tend to think that applications that have been largely installed are trustworthy and performant. In this case, both spyware show a big user population, yet have no reviews. We believe the hacker used an install farm or mobile device emulators to fake those numbers, hence making its applications better ranked in stores’ category lists and increase their apparent legitimacy.
- Requiring less user interaction: Often, users install applications they end up not even using. For most malware, that means the attack is unsuccessful. To overcome that obstacle, File Manager and File Recovery & Data Recovery can, through the advanced permissions they use, induce the restart of the device. This then permits the apps to launch and execute themselves automatically at restart.
- Preventing uninstallation: It is common to believe that on a mobile device, all applications are visible on the home screen. Although, that’s not the case and an application can simply hide its icon from the general view. Both of these malware use this technique to make their uninstallation harder. To delete them, users require going to the application list in the settings.
Our security recommendations
First, we advise anyone using these applications to delete them.
As an individual
- Do not download applications that do not have any reviews while thousands of users.
- Read reviews when there are any, they usually reflect the applications true nature.
- Always carefully read permissions before accepting them.
As an organization
- Sensibilize collaborators on mobile threats.
- Automate mobile detection and response to offer a secure flexibility to users, by vetting applications and preventing their launch when non-compliant with your security policy.



.png)


