Update: The application has finally been removed from Google Play on January 27th, after staying available on the store for 15 days.
Pradeo’s researchers discovered a malicious mobile application called 2FA Authenticator distributed on Google Play and installed by 10K+ users. We identified the application as a trojan-dropper as it is leveraged by cybercriminals to secretly install malware on users’ mobile devices. Our analysis revealed that the dropper automatically installs a malware called Vultur which targets financial services to steal users’ banking information. Users of this app are advised to delete it immediately; we have alerted the Google Play team of our discovery.
Application ID
https://play.google.com/store/apps/details?id=com.privacy.account.safetyapp
2FA Authenticator
com.privacy.account.safetyapp
Version 1.0
10,000+ installs
A well-concealed malicious application
The application called 2FA Authenticator is a dropper leveraged to spread malware on its users’ devices. It has been developed to look legitimate and provide a real service. To do so, its developers used the open-source code of the official Aegis authentication application to which they injected malicious code. As a result, the application is successfully disguised as an authentication tool which ensures it maintains a low profile.
An automated attack in two stages
First stage of the attack: profiling
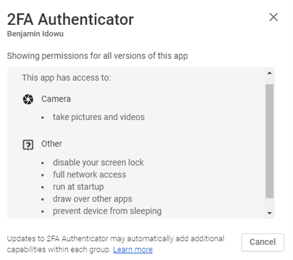
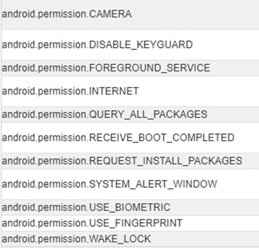
Unlike the official Aegis application it was conceived after, 2FA Authenticator requests critical permissions that it does not disclose on its Google Play profile.
These hidden permissions and the malicious code the application executes enable it to automatically:
- Collect and send users’ application list and localization to its perpetrators, so they can leverage the information to perform attacks targeted towards individuals in specific countries that use specific mobile applications, instead of massive untargeted attack campaigns that would risk exposing them,
- Disable the keylock and any associated password security,
- Download third-party applications under the shape of alleged updates ,
- Freely perform activities even when the app is shut off,
- Overlay other mobile applications’ interface using a critical permission called SYSTEM_ALERT_WINDOW for which Google specifies “Very few apps should use this permission; these windows are intended for system-level interaction with the user.”
| 2FA Authenticator permissions disclosed on Google Play | 2FA Authenticator permissions requested |
 |
 |
Second stage of the attack: banking malware installation
Our researchers found out that the second stage of the attack is conditioned to the information the dropper first collects on its users. When some conditions are met, our analysis revealed that the dropper installs Vultur, an advanced and relatively new kind of malware that mostly targets online banking interface to steal users’ credentials and other critical financial information.
A user review alerting about the malicious behavior.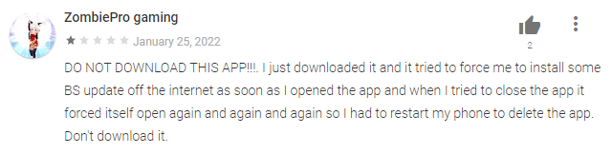
Please do not confuse this malicious application with 2FA Authenticator (2FAS), package: com.twofasapp.
They are different apps.


.png)


