The applications they offer are copies of official applications, but under the guise of offering free-of-charge use of Netflix, Spotify, ExpressVPN, Avira Antivirus, The Guardian, etc., they often infect mobile devices with malware, spyware and adware unbeknownst to their users.
Code vulnerabilities and the lack of security best practices make it easy for hackers to copy and inject code in applications. Mobile applications injected with malware are often promoted to users through ads displayed in applications downloaded from official app stores, or through phishing campaigns. By impersonating reliable apps, counterfeited apps mislead users to steal their personal information and commit fraud.
The lucrative business of modified applications
Alternative application stores are so in demand that in 2020, three of them were more prolific than Google Play and the App store in terms of newly posted applications yearly (source: RiskIQ).
Modified applications, also called MOD, are copies of original applications to which changes are made by third-party/unofficial developers to add features or unlock premium subscription.
During the tampering, most of MODs are injected with malicious code to spy on users by accessing their gallery, contacts, digital wallets, etc…, exfiltrate their data and display untimely ads. Stolen data are then sold on the dark web.
-png.png?width=700&name=MicrosoftTeams-image%20(17)-png.png)
-png.png?width=700&name=MicrosoftTeams-image%20(18)-png.png)
Beware of fake Netflix applications
Netflix is a thriving business in which cybercriminals see an opportunity to make money. Our team has identified online hundreds of modified versions of the original Netflix application.
More than simply usurping the company’s name and/or logo like the FlixOnline app did (discovered on Google Play in April 2021 and removed afterwards), the interface of the fake Netflix apps we found look nearly the same as older versions of the original Netflix app.
When performing a security analysis of these fake apps with the Pradeo Security engine, it appears that they have been injected with malware, spyware and/or adware. Besides, the featured malicious programs (Remote-Access-Tool, smishing trojan, rootkit…) do not require a device to be rooted to breach it, hence maximizing its reach.
Overview of one of the fake Netflix application:

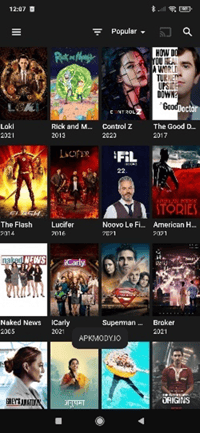
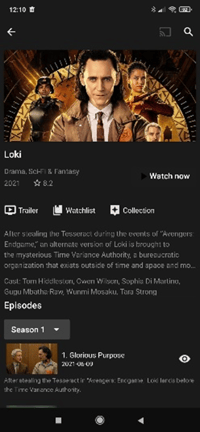
Comparing the official app’s code to modified ones highlights that despite most folders and files being similar, some new content has been added. Looking deeper, we found new ad libraries, JavaScript code to reach external servers and commands to download new APKs onto the device.
A known vulnerability exploited to inject malicious code
Among Pradeo’s database composed of millions of public iOS and Android applications’ security report, 57% of apps are vulnerable to code tampering, as classified as #8 in the OWASP top 10 for mobile.
Typically, third-party developers exploit this vulnerability when found in official applications to tamper them to offer free services. Then, they take advantage of these apps’ popularity to have users installing them from unofficial app stores or trick them via phishing attacks.
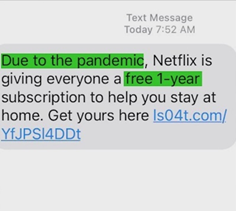
Example of two phishing campaigns promoting a fake Netflix application:
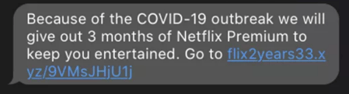
Our recommendations
As a developer, how to prevent my application from being tampered?
- Obfuscate and encrypt your code to discourage hackers.
- Enhance your app with a tamper detection feature that will react appropriately at runtime to a code integrity violation.
As a user, how to avoid fake apps?
- Beware of smishing (SMS phishing) campaigns.
- Do not trust offers that seem too good to be true.
- Do not download applications displayed in ads, but instead look for them in official stores.
- Only download applications from Google Play and App Store.



.png)


